搜索结果: 1-15 共查到“NIST”相关记录46条 . 查询时间(0.048 秒)
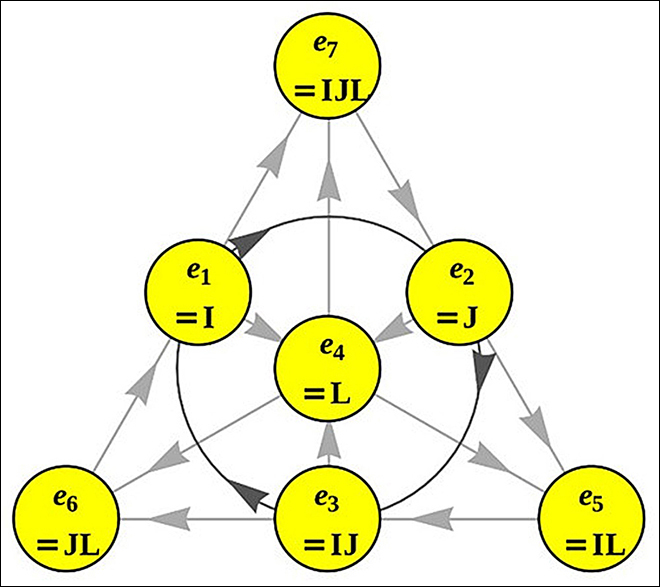
攻破NIST后量子密码标准候选算法HK17研究(图)
NIST HK17 线性方程
2021/8/11
美国国家标准与技术研究院(National Institute of Standards and Technology,NIST)于2016年面向全球征集抗量子密码算法标准。经过近一年的征集及形式审查,NIST于2017年12月公布了69个算法作为首轮候选算法。随后,NIST启动了对入选算法的评估工作。在组织人力对入选算法进行内部评估的同时,NIST也面向全球公开征集对这些算法的外部评估。密钥交换...
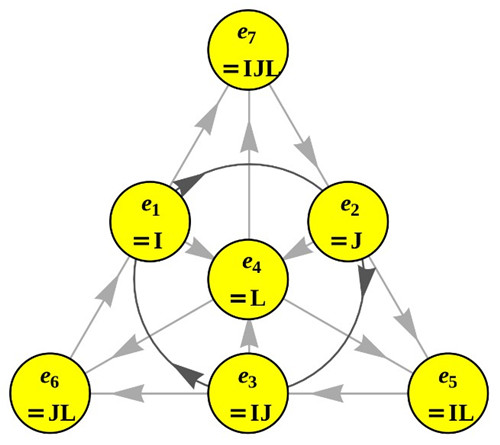
攻破NIST后量子密码标准候选算法HK17研究进展(图)
密钥交换算法 通信密钥 HK17 八元数
2021/9/1
美国国家标准与技术研究院(National Institute of Standards and Technology,NIST)于2016年面向全球征集抗量子密码算法标准。经过近一年的征集及形式审查,NIST于2017年12月公布了69个算法作为首轮候选算法。随后,NIST启动了对入选算法的评估工作。在组织人力对入选算法进行内部评估的同时,NIST也面向全球公开征集对这些算法的外部评估。
近年来,量子计算机技术发展迅速,它对传统公钥密码算法的安全性带来了潜在的巨大威胁。因此,美国、中国、欧盟等世界主要国家和地区纷纷开始研制抗量子计算机攻击的密码算法。其中,美国国家标准与技术研究院(National Institute of Standards and Technology,NIST)于2016年面向全球征集抗量子密码算法标准,并于2017年底完成了首轮候选算法的征集工作。
In this paper we present our observations about NIST's Compression estimate test given in SP-800 90B. We observe that steps 4 and 7 of the test may be re-framed to gain efficiency. Based on our observ...
The Power of NIST Cryptographic Statistical Tests Suite
Statistical testing Cryptographic evaluation Random bit generators
2019/8/8
This paper is focused on an open question regarding the correlation and the power of NIST statistical test suite. If we found some correlation between these statistical tests, then we can improve the ...
This paper presents pqm4 – a testing and benchmarking framework for the ARM Cortex-M4. It makes use of a widely available discovery board with 196 KiB of memory and 1 MiB flash ROM. It currently inclu...
Hardware Implementations of NIST Lightweight Cryptographic Candidates: A First Look
Lightweight cryptography FPGA Authenticated cipher
2019/7/17
Security in the Internet of Things (IoT) is challenging. The need for lightweight yet robust cryptographic solutions suitable for the IoT calls for improved design and implementation of constructs suc...
Optimized implementation of the NIST PQC submission ROLLO on microcontroller
post-quantum cryptography optimization embedded system
2019/7/15
We present in this paper an efficient implementation of the code-based cryptosystem ROLLO, a candidate to the NIST PQC project, on a device available on the market. This implementation benefits of the...
Exploiting Determinism in Lattice-based Signatures - Practical Fault Attacks on pqm4 Implementations of NIST candidates
Deterministic Lattice Signatures pqm4 Fault Attack
2019/7/8
In this paper, we analyze the implementation level fault vulnerabilities of deterministic lattice-based signature schemes. In particular, we extend the practicality of skip-addition fault attacks thro...
Exploring NIST LWC/PQC Synergy with R5Sneik: How SNEIK 1.1 Algorithms were Designed to Support Round5
Post-Quantum Cryptography Lightweight cryptography Permutation-Based Cryptography
2019/6/12
Most NIST Post-Quantum Cryptography (PQC) candidate algorithms use symmetric primitives internally for various purposes such as ``seed expansion'' and CPA to CCA transforms. Such auxiliary symmetric o...
A note on the correlations between NIST cryptographic statistical tests suite
statistical testing cryptographic evaluation random bit generators
2019/5/24
This paper is focused on an open question regarding the correlation and the power of the NIST statistical test suite. If we found some correlation between these statistical tests, then we can improve ...
An Efficient and Compact Reformulation of NIST Collision Estimate Test
IID Non-IID Min Entropy
2019/5/14
In this paper we give an efficient and compact reformulation of NIST collision estimate test given in SP-800 90B. We correct an error in the formulation of the test and show that the test statistic ca...
A Complete and Efficient Key Mismatch Attack on NIST Candidate NewHope
key encapsulation mechanism NIST Candidate NewHope
2019/4/29
In CT-RSA 2019, Bauer et al. have analyzed the case when the public key is reused for the NewHope key encapsulation mechanism (KEM), a second-round candidate in the NIST Post-quantum Standard process....
NIST Post-Quantum Cryptography- A Hardware Evaluation Study
Post-Quantum Cryptography Hardware Implementation
2019/1/26
Experts forecast that quantum computers can break classical cryptographic algorithms. Scientists are developing post quantum cryptographic (PQC) algorithms, that are invulnerable to quantum computer a...
Side-channel Assisted Existential Forgery Attack on Dilithium - A NIST PQC candidate
Dilithium Lattice based cryptography Digital Signatures
2018/11/19
The recent lattice-based signature scheme Dilithium, submitted as part of the CRYSTALS (Cryptographic Suite for Algebraic Lattices) package, is one of a number of strong candidates submitted for the N...

