搜索结果: 1-15 共查到“turning”相关记录88条 . 查询时间(0.061 秒)
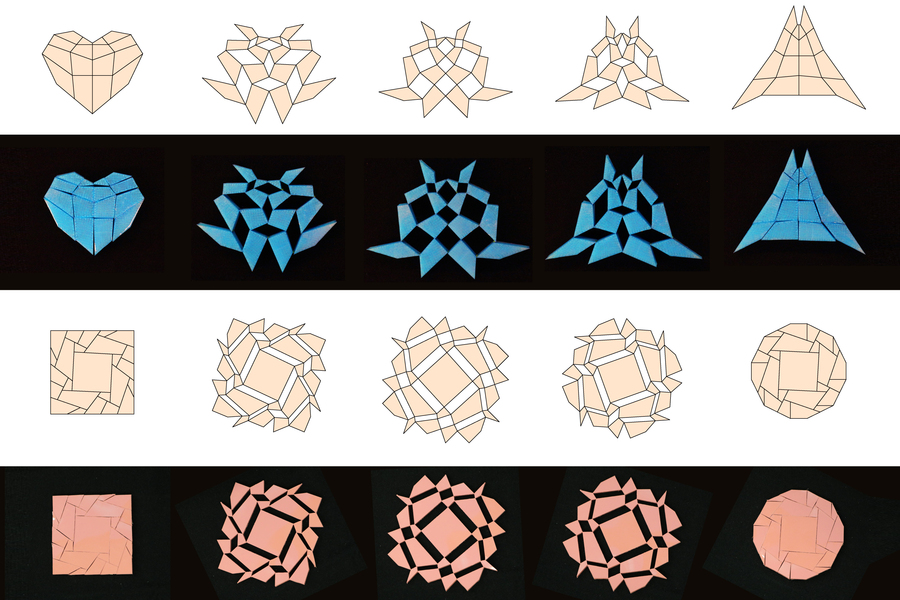
Turning a circle into a square is possible with this kirigami-inspired formula(图)
kirigami 圆形 正方形 几何
2023/6/5

Turning carbon emissions into rocks(图)
碳排放 岩石 清洁能源 气候学
2023/7/7
Designed from Recycled: Turning Polyethylene Waste to Covalently Attached Polylactide Plasticizers
HDPE Oxidative degradation Feedstock recycling PLA Plasticization
2024/3/8
High-density polyethylene (HDPE) waste was successfully feedstock recycled, and the obtained chemicals were utilized for synthesis of plasticizers for polylactide (PLA). First, an effective route to r...

Lake Erie's toxic algae blooms:Why is the water turning green?(图)
Lake Erie toxic algae water turning green
2019/11/22
Since the late 1990s, Lake Erie has been plagued with blooms of toxic algae that turn its waters a bright blue-green. These harmful algae blooms are made up of cyanobacteria that produce the liver tox...
Turning HATE Into LOVE: Homomorphic Ad Hoc Threshold Encryption for Scalable MPC
MPC threshold encryption obfuscation
2018/11/5
We explore large-scale fault-tolerant multiparty computation on a minimal communication graph. Our goal is to be able to privately aggregate data from thousands of users - for example, in order to obt...

Winter Road Salt,Fertilizers Turning North American Waterways Increasingly Saltier(图)
Winter Road Salt Fertilizers Turning North American Waterways Increasingly Saltier
2018/1/10
Across North America, streams and rivers are becoming saltier, thanks to road deicers, fertilizers and other salty compounds that humans indirectly release into waterways. At the same time, freshwater...
Lattice Klepto: Turning Post-Quantum Crypto Against Itself
Post-quantum cryptography kleptography lattice-based encryption NTRU
2017/11/28
This paper studies ways to backdoor lattice-based systems following Young and Yung's work on backdooring RSA and discrete-log based systems. For the NTRU encryption scheme we show how to build a backd...
On the Easiness of Turning Higher-Order Leakages into First-Order
side-channel analysis masking higher-order
2017/3/31
Applying random and uniform masks to the processed intermediate values of cryptographic algorithms is arguably the most common countermeasure to thwart side-channel analysis attacks. So-called masking...
IKP: Turning a PKI Around with Blockchains
public-key infrastructures blockchain smart contracts
2016/12/8
Man-in-the-middle attacks in TLS due to compromised CAs have been mitigated by log-based PKI enhancements such as Certificate Transparency. However, these log-based schemes do not offer sufficient inc...
CAESAR has caused a heated discussion regarding the merits of one-pass encryption and online
ciphers. The latter is a keyed, length preserving function which outputs ciphertext blocks as soon as the ...
CAESAR has caused a heated discussion regarding the merits of one-pass encryption and online
ciphers. The latter is a keyed, length preserving function which outputs ciphertext blocks as soon as the ...
Revisiting Turning Online Cipher Off
symmetric-key cryptography cryptanalysis SPRP security
2015/12/23
In 'Turning Online Ciphers Off', a class of constructions was defined based on layers of secure online ciphers interleaved with simple mixing layers (like reversing and block-shifting). Here we show t...
Turning the rumor of the May 11, 2011, earthquake prediction in Rome, Italy, into an information day on earthquake hazard
Seismic hazard Education and outreach Seismic risk reduction
2015/8/26
A devastating earthquake was predicted to hit Rome on May 11, 2011. This prediction was never officially released, but it grew on the internet and was amplified by the media. It was erroneously ascrib...
Turning a Shove into a Nudge? A "Labeled Cash Transfer" for Education
Human capital investment government management marked as cash transfers education plan
2015/7/20
Conditional Cash Transfers (CCTs) have been shown to increase human capital investments, but their standard features make them expensive. We use a large randomized experiment in Morocco to estimate a...
Measurement and Comparison of Taekwondo and Yongmudo Turning Kick Impact Force for Two Target Heights
Turning kick impact force Taekwondo Yongmudo
2015/4/30
The primary purpose of this research was to compare the impact characteristics of Taekwondo (TKD) and Yongmudo (YMD) player’s turning kick according to the target height. 5 highly skilled YMD and 5 TK...


